There’s no doubt that securing printers and print environments is more critical than ever. From sophisticated cyber threats to unauthorized access, printers are a favorite target of hackers. Toshiba’s innovative and holistic approach ensures robust protection across every touchpoint of the printing process. In this blog, we’ll look at the ways Toshiba protects your data throughout the printing process, making sure your information stays secure from start to finish.
Fleet-Wide Security Administration
Managing a fleet of printers can be daunting, but Toshiba simplifies this with fleet-wide security administration. By centralizing security measures, they ensure that all devices within a printing fleet are uniformly protected. Notably, Toshiba manufactures its own hard disk drives (HDDs) for its multifunction printers (MFPs). These HDDs are fortified with unique technology, making them some of the most secure storage devices available today.
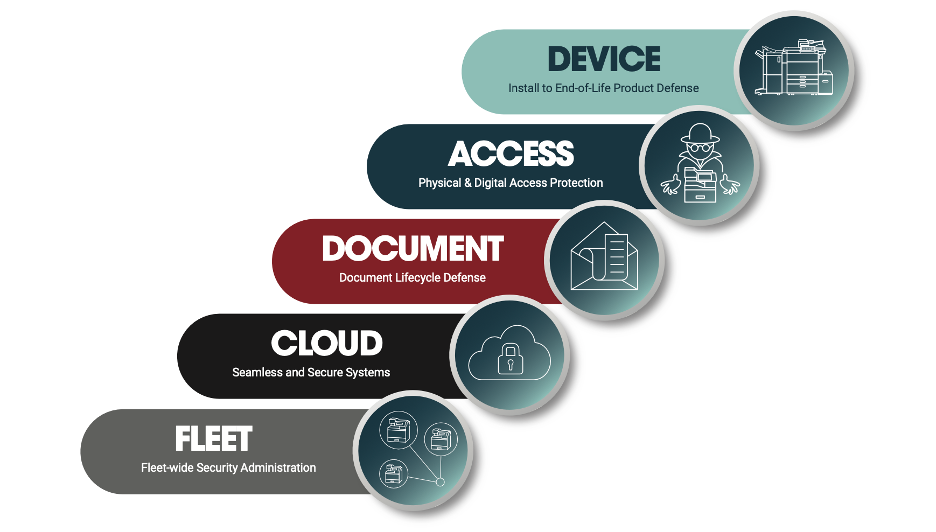 The Elevate Sky service adds another layer of protection. This suite of cloud-based applications and services enables remote monitoring and management of Toshiba MFPs. Administrators can create and deploy security policies fleet-wide via the Toshiba cloud. Any policy violations are flagged and promptly notified to the administrator, ensuring real-time compliance.
The Elevate Sky service adds another layer of protection. This suite of cloud-based applications and services enables remote monitoring and management of Toshiba MFPs. Administrators can create and deploy security policies fleet-wide via the Toshiba cloud. Any policy violations are flagged and promptly notified to the administrator, ensuring real-time compliance.
Seamless and Secure Cloud Systems
Toshiba’s integration of cloud-based solutions ensures seamless and secure processing, storage, and access to data. By leveraging secure cloud services, they enhance system reliability and security. This integration eliminates the traditional barriers to secure data handling, offering an efficient and resilient print environment.
The cloud systems employed by Toshiba are designed to withstand modern cyber threats while providing easy accessibility. This balance of security and usability makes it an ideal choice for businesses looking to streamline their operations without compromising on security.
Document Lifecycle Defense
Protecting sensitive information throughout its lifecycle is paramount for businesses. Toshiba’s document lifecycle defense strategy focuses on this very aspect. From the moment a document is created until its disposal, robust security measures are in place to maintain confidentiality and integrity.
The strategy covers three key areas:
- Capture: Ensuring secure creation and capture of documents.
- Store: Implementing secure retention policies to prevent unauthorized access or leaks.
- Deliver: Guaranteeing secure delivery and output of documents.
This comprehensive approach ensures that sensitive information remains protected at every stage of its lifecycle.
Physical and Digital Access Protection
Access control is a critical component of security. Toshiba prioritizes both physical and digital access protection to its printing devices and documents. By implementing stringent security measures, they ensure that only authorized personnel can access sensitive information and devices.
Physical access controls prevent unauthorized individuals from physically accessing printers and other devices. Meanwhile, digital access controls safeguard against cyber threats, ensuring that digital data and documents are equally protected. This dual-layered approach fortifies the overall security posture of the print environment.
Install to End-of-Life Product Defense
Security doesn’t end with installation. Toshiba’s product defense strategy spans from the initial setup of printing devices to their end-of-life phase. Security features and updates are consistently incorporated throughout the product lifecycle to mitigate vulnerabilities.
From regular firmware updates to end-of-life disposal procedures, Toshiba ensures continuous protection against evolving threats. This ongoing commitment to security provides businesses with peace of mind, knowing their print environment is always protected.
Final Words
Toshiba’s holistic approach to print security addresses every aspect of the print environment, from devices and documents to access control and cloud integration. By emphasizing comprehensive protection, they provide businesses with the tools to safeguard their sensitive information.
About Proven IT
Proven IT helps organizations leverage technology to boost productivity, control costs and protect confidential data. Headquartered in Illinois with customers throughout the United States, popular solutions include Managed IT, Cybersecurity, Managed Office Services, Integrated Voice & Data, Physical Security Systems and Business Process Automation






