Many business leaders breathe easier once they purchase a cyber insurance policy. On paper, it appears to be a safety net against ransomware, phishing scams, or data breaches. But in reality? Cyber insurance exclusions can leave dangerous gaps in your protection.
Many companies only realize what’s not covered after an incident has occurred. By then, it’s too late. This post will help you:
- Spot the most common cyber insurance exclusions
- Understand how they impact your cyber insurance coverage
- Learn practical steps to keep your business safe, without fear or jargon
With a little foresight (and the right partner), you can ensure your coverage aligns with your real-world risks.
What Are Cyber Insurance Exclusions?
Cyber insurance exclusions are the “fine print” conditions that limit when and how your insurance applies. Insurers often exclude certain types of attacks, actions, or oversights — leaving you exposed if those are the very scenarios you face.
Not all cyber insurance policies are the same. Sometimes, even when something looks covered, claims are often delayed or denied if your IT environment doesn’t meet insurer standards. Below are seven exclusions that often catch businesses off guard, and how Proven IT helps close the gap.
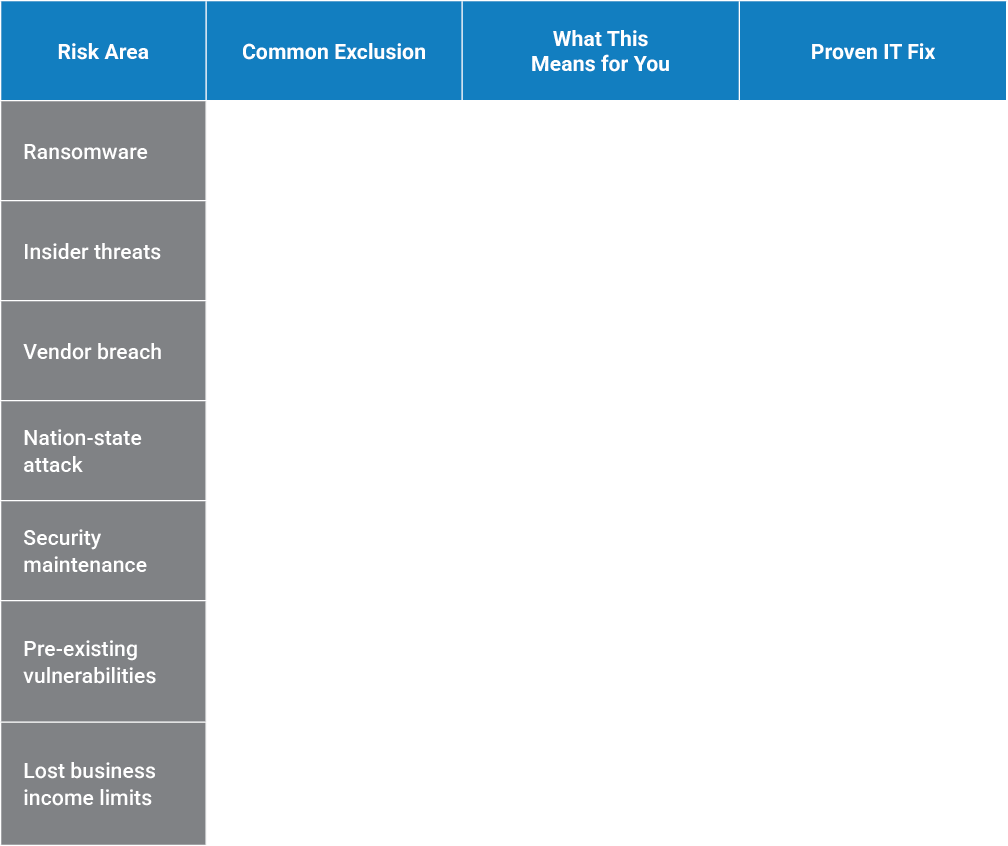
1. Ransomware Payments Above Policy Limits
Ransomware-as-a-service has made attacks more common, and payouts are skyrocketing. Many policies cap reimbursements well below the actual demand, leaving businesses to cover the remaining costs. Without strong defenses and recovery plans, that gap can be devastating.
Proven IT Fix: We perform ransomware readiness testing and develop secure, documented backup strategies, enabling you to recover quickly and meet insurer expectations.
2. Insider Threats
It doesn’t take a malicious hacker to cause damage. An employee who clicks a phishing link or a disgruntled ex-staffer with lingering access can trigger massive losses. Yet, many policies exclude insider-driven incidents entirely.
Proven IT Fix: Insider risk training, access controls, and ongoing monitoring stop threats at the source and provide documentation to prove compliance.
3. Third-Party Vendor Breaches
If your payroll provider, software vendor, or cloud host suffers a breach, insurers often put the liability back on you. That means you’re responsible for costs, reputational damage, and lost trust.
Proven IT Fix: Proven IT performs vendor risk assessments and ongoing third-party monitoring to minimize exposure from your supply chain.
4. Nation-State Attacks
When attacks are tied to foreign governments, insurers often classify them as “acts of war.” Translation: no coverage. Unfortunately, these attacks don’t just target federal agencies; they can also hit private businesses.
Proven IT Fix: Advanced detection, defense strategies, and real-time monitoring keep you ahead of sophisticated, state-linked threats.
5. Failure to Maintain Security Standards
Many policies require specific security controls, such as MFA, encryption, and employee training. If there is missing documentation to prove those controls were in place, insurers may deny your claim.
Proven IT Fix: Proven IT aligns your environment with insurer requirements and provides the documentation you’ll need at claim time.
6. Pre-Existing Vulnerabilities
If a breach stems from a known vulnerability you didn’t patch, your claim could be rejected. Insurers expect businesses to actively manage risks — not leave them unaddressed.
Proven IT Fix: We run ongoing vulnerability scans, apply patches, and keep your systems compliant so you’re never blindsided by an exclusion.
7. Lost Business Income Beyond a Time Limit
Cyber incidents can disrupt business for months, but most policies only cover 30–60 days of lost income. After that, recovery costs are on you.
Proven IT Fix: Business continuity planning and disaster recovery strategies help you minimize downtime well beyond the limits of insurance.
Coverage Gap Reality Map
Protect Your Business With Proven Cybersecurity Services
Schedule a 30-minute consultation today to see how Proven IT’s cybersecurity experts can help you reduce risk, train your team, and stay ahead of evolving threats. From endpoint and email protection to phishing simulations, 24/7 monitoring, and proactive risk management, we’ll design a security strategy that fits your business — and keeps it resilient all year long.

Why Choose Proven IT to Bridge Cyber Insurance Gaps
Cyber insurance coverage is a smart move, but it’s only as strong as the IT environment behind it. Claims are often delayed or denied if businesses can’t meet an insurer’s security and documentation standards.
Proven IT specializes in aligning your cyber insurance policy with your actual IT defenses, so coverage applies when you need it most. Beyond just meeting requirements, we help you minimize risks insurers won’t cover. Here’s how:
- Compliance-Backed IT Services: We align your security controls with insurer expectations (such as MFA, encryption, and endpoint protection) so your coverage stands up to scrutiny.
- Insurer-Ready Documentation: From system logs to training records, we provide the proof insurers require before renewal or claim time.
- Continuous Threat Monitoring: Cybercriminals don’t take days off. We monitor, patch, and protect your environment against ransomware, phishing, and insider threats.
- Vendor Risk Assessments: We identify vulnerabilities in your supply chain and close gaps your policy may exclude.
- Business Continuity Planning: We help you recover faster than insurance time limits allow, reducing downtime and uncovered losses.
Start Closing Cyber Insurance Gaps with Proven IT
The most effective way to protect your business is to ensure that your policy and IT environment work in tandem. With Proven IT, you’ll uncover hidden exclusions, strengthen your defenses, and gain peace of mind knowing you’re fully protected when it matters most.