The internet is vast, but not all of it is accessible through standard search engines like Google. Beneath the surface lies the Dark Web—a hidden part of the internet that is often associated with illegal activities. While it has legitimate uses, it is also a hub for cybercriminals who buy and sell stolen data, including company credentials.
For businesses, the Dark Web poses a significant threat. It’s where hackers exploit stolen credentials to access company networks, deploy ransomware, and commit fraud. Ignoring the risks can lead to financial losses, reputational damage, and legal consequences. Proven IT’s Dark Web solution helps businesses stay ahead of these threats by continuously monitoring for compromised credentials and providing actionable intelligence.
Read on to learn more about the Dark Web and how cybercriminals use it, the risks it poses to your business, and how Proven IT’s Dark Web threat protection can help keep your organization safe from potential threats.
What Is the Dark Web?
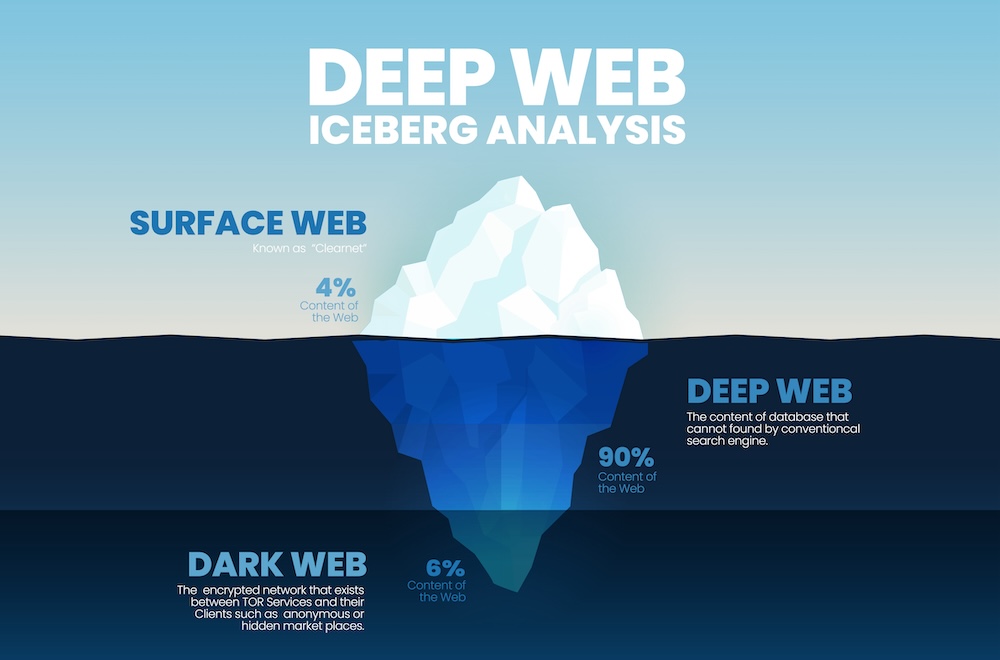
The internet is divided into three layers: the surface web, the deep web, and the Dark Web. The surface web includes public websites indexed by search engines. The deep web consists of private sites, such as email accounts, banking portals, and internal business databases, that require login credentials. The Dark Web, however, is an unregulated space that can only be accessed using special tools like Tor or I2P.
The Dark Web provides anonymity to its users, which makes it attractive to journalists, activists, and privacy-conscious individuals. Unfortunately, this same anonymity is exploited by cybercriminals to conduct illicit activities.
How Cybercriminals Use the Dark Web
The Dark Web is home to underground marketplaces where hackers trade stolen data and cybercrime tools. Some of the most common threats include:
- Stolen Credentials & Data Breaches: Login information from businesses is sold in bulk, often allowing attackers to bypass security measures. These credentials may come from phishing attacks, malware infections, or large-scale corporate data breaches. Once in the wrong hands, they can be used to access sensitive company information, steal funds, or spread malware.
- Ransomware-as-a-Service: Cybercriminals rent out ransomware tools, making it easy for even inexperienced hackers to launch attacks. These ready-made ransomware kits allow criminals to demand ransom payments from businesses in exchange for regaining access to their encrypted data.
- Corporate Espionage & Insider Threats: Disgruntled employees or competitors may sell confidential company data on the Dark Web. Trade secrets, financial records, and proprietary information can be exploited to gain an advantage or cause financial harm.
- Phishing Kits & Malware: Hackers distribute malicious software and phishing kits designed to steal login credentials, credit card details, and personal information. These tools make it easier for cybercriminals to launch large-scale phishing attacks that can compromise entire organizations.
- Botnets & Automated Attacks: The Dark Web facilitates the buying and selling of botnets, which are networks of infected computers controlled by cybercriminals. These botnets can be used to launch large-scale denial-of-service (DDoS) attacks, send spam emails, or carry out automated hacking attempts.
- Black Market for Stolen Data: Cybercriminals on the Dark Web buy and sell a variety of stolen data, including bank account details, Social Security numbers, medical records, and business financial information. This data can be used for fraud, identity theft, or resold to other criminals.
SMBs are particularly vulnerable because they often lack the resources to monitor these threats. Attackers know this and frequently target small to mid-sized businesses that may not have sophisticated cybersecurity defenses.
What This Means for Your Business
A company’s digital security is only as strong as its weakest link. If an employee’s login credentials are leaked on the Dark Web, attackers can use them to infiltrate the network. The consequences of such breaches can be severe:
- Financial Losses: Recovering from a cyberattack can cost businesses millions of dollars in ransom payments, legal fees, and system repairs. Beyond direct financial costs, companies may experience operational downtime, lost revenue, and the expenses associated with strengthening security after an attack.
- Reputational Damage: Customers lose trust in companies that suffer security breaches. A compromised business may struggle to retain clients and attract new customers if it fails to demonstrate strong cybersecurity practices. The long-term impact on brand reputation can be difficult to recover from.
- Regulatory Penalties: Non-compliance with data protection laws like GDPR, HIPAA, and CCPA can result in hefty fines. Governments and regulatory bodies hold businesses accountable for protecting customer data, and failure to do so can lead to legal action and significant financial penalties.
- Loss of Intellectual Property: If cybercriminals gain access to proprietary business data, trade secrets, or research and development information, competitors or malicious actors could exploit it. This can weaken a company’s market position and lead to lost business opportunities.
- Supply Chain Vulnerabilities: Many businesses rely on third-party vendors and suppliers, which can introduce security risks. If a supplier’s credentials are exposed on the Dark Web, it may create a backdoor into your systems, compromising sensitive data and operations.
- Employee and Customer Data Exposure: Cybercriminals often target personal information belonging to employees and customers. Stolen Social Security numbers, addresses, and financial data can lead to identity theft and fraud, further eroding trust in a company’s ability to protect sensitive information.
Ignoring Dark Web threats is not an option. Businesses must be proactive in monitoring for compromised credentials and implementing security measures to prevent unauthorized access. Investing in Dark Web monitoring and cybersecurity solutions is a critical step in reducing risk and ensuring long-term protection.
How Proven IT’s Dark Web Monitoring Protects Businesses

Proven IT’s Dark Web threat monitoring provides powerful intelligence and peace of mind. Always-on human and machine monitoring using real-time, analyst-validated data goes to work immediately to protect your business from credential compromise risks.
Comprehensive, Validated Data
- Gain valuable intelligence to identify and address security gaps with accurate data on compromised company credentials found on the Dark Web.
- Get additional protection from unpleasant surprises with credential monitoring for your supply chain and for the personal email addresses of your executive and administrative users, reducing the risk from cybercriminals gaining access to a privileged account.
Our analysis delves into every corner of the Dark Web, including:
- Hidden chat rooms
- Unindexed sites
- Private websites
- P2P (peer-to-peer) networks
- IRC (internet relay chat) channels
- Social media platforms
- Black market sites
- 640,000+ botnets
With this level of deep visibility, Proven IT helps your business stay ahead of emerging threats before they turn into costly breaches. By proactively monitoring compromised credentials across hidden corners of the Dark Web, PIT provides the insights you need to strengthen your security posture and safeguard your most critical assets.
Steps Businesses Can Take to Stay Protected
Monitoring the Dark Web is just one part of a robust cybersecurity strategy. Businesses should also take additional steps to protect their data:
- Regular Security Assessments: Conduct frequent security audits to identify weaknesses before attackers exploit them.
- Dark Web Monitoring: Ensure constant vigilance against leaked credentials and potential threats.
- Multi-Factor Authentication (MFA): Enforce MFA on all company accounts to prevent unauthorized access, even if passwords are compromised.
- Employee Training: Provide ongoing cybersecurity training to help staff recognize and avoid phishing attacks and social engineering scams.
- Incident Response Plan: Develop a detailed incident response plan outlining the steps to take in case of a breach, including containment, investigation, and recovery.
- Data Encryption and Backup: Encrypt sensitive data and regularly back up critical files to prevent data loss and minimize damage from ransomware attacks.
- Network Segmentation: Limit access to sensitive systems and data by segmenting networks, reducing the impact of potential breaches.
Stay Ahead of Cyber Threats
Cyber threats are evolving, and businesses cannot afford to be reactive. The Dark Web is a growing marketplace for stolen data, making it imperative for companies to actively monitor and protect their credentials.
Proven IT’s Dark Web solution provides businesses with the intelligence they need to stay ahead of cybercriminals. By leveraging real-time monitoring, validated data, and expert insights, companies can reduce their risk and avoid costly breaches.
About Proven IT
Proven IT helps organizations leverage technology to boost productivity, control costs and protect confidential data. Headquartered in Illinois with customers throughout the United States, popular solutions include Managed IT, Cybersecurity, Managed Office Services, Integrated Voice & Data, Physical Security Systems and Business Process Automation.






